Many daily data and system breaches around the world result from stolen, weak or reused passwords. Users need a password for almost every site and app they use now.
Our personal lists of them are becoming unwieldy, and it’s not uncommon for someone to have over 100 passwords.
But it’s easier than you think to crack commonly-used passwords.
As with the other recommendations in this series, you should adhere to these practices even if you aren’t required to. See the chart below for an idea of the speed of cracking based on a hacker “brute forcing” the password “hashes.”
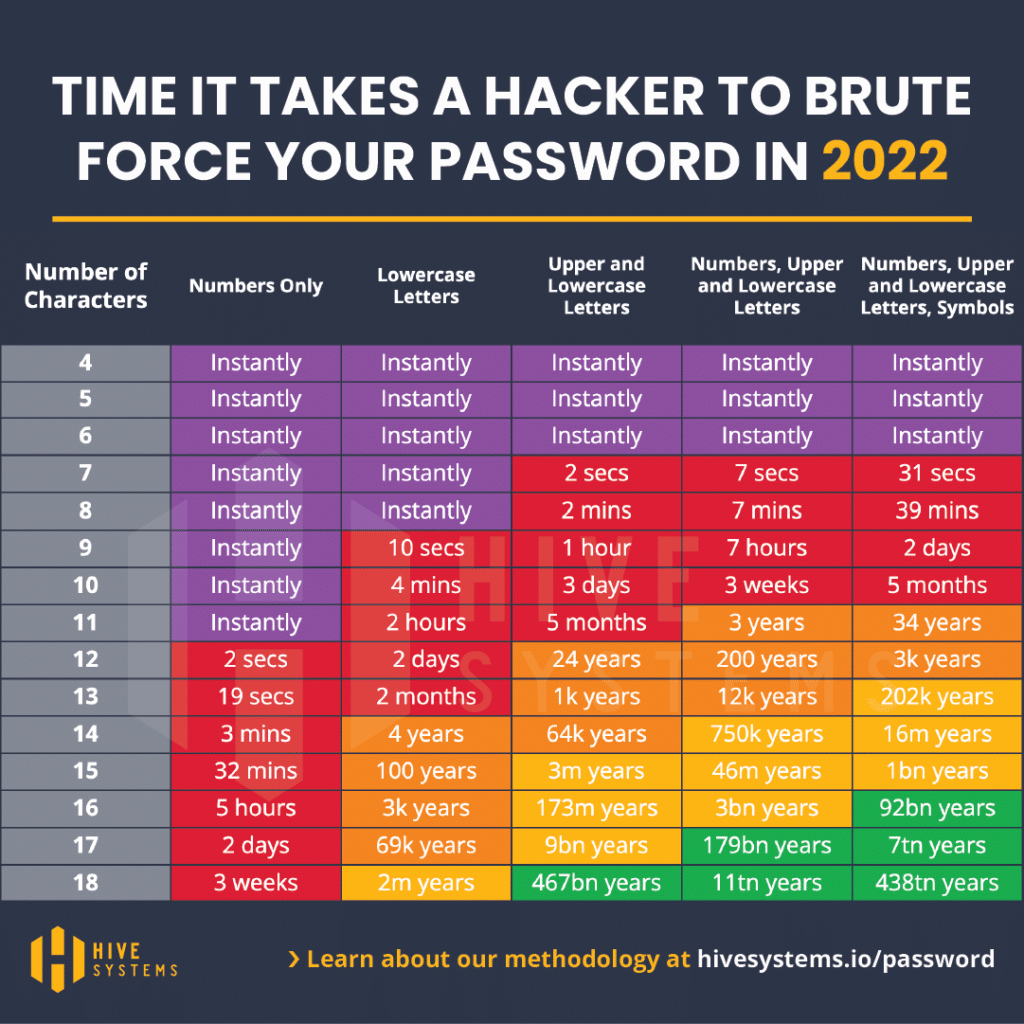
Hive Systems created this well-known chart that shows how long a hacker would take to “brute force” their way into an account.
Generally, moving to the right, increasing password character length and complexity makes breaking the password progressively harder. This is the most recent version of this chart.
So What is Brute Forcing?
From Wikipedia:
“Brute-force attacks work by calculating every possible combination that could make up a password and testing it to see if it is the correct password. As the password’s length increases, the amount of time, on average, to find the correct password increases exponentially.”
Passwords are generally saved on servers and other computers as hashes, which are passwords run through a one-way program (or “function”).
Passwords are scrambled after running through the function to look something like this: 5f4dcc3b5aa765d61d8327deb882cf99 –which is the hash of the word “password” and since it’s one way, it can’t be reverse computed.
The hacker gets these hashes and runs them through automated software that generates a large number of consecutive guesses as to the value of the desired data.
So the longer the password the longer it takes to break it and the better protection it will give you!
Some Guidelines
If you want to create strong passwords according to the chart above, you should follow a few guidelines. The rules below should apply to personal or business passwords and can avoid some password bad habits:
1. Use a minimum length of at least twelve characters and include at least one each of a number, an uppercase letter, a lowercase letter and a symbol, if permitted.
That will put you in the last column of the chart above and safely in the orange for 3000 years to crack.
2. Never use consecutive identical, all-numeric or all-alphabetic characters. As shown in the chart, using characters like this in a password makes it easier to break.
3. Never use words from a dictionary. Hackers may use a type of brute force attack called a dictionary attack, where passwords are cracked using a list of common words found in a dictionary.
4. Never use real personal data in your passwords, e.g. names, birthdays, phone numbers and other personal details.
5. Never use patterns in passwords.
6. Never use passwords that are easy to remember.
7. Never use real personal data in identity questions (hints) used for password recovery.
Next, we look at proper and safe password practices.
***
Tech Kahunas is a San Diego Managed IT Services provider which provides IT support and services like 24/7 monitoring, data backup and restore, and malware protection.
Tech Kahunas will help you Defend Your Island. Set up a free 30-minute Strategy Session with us now.



 Get your CPA firm aquainted with new FTC rules.
Get your CPA firm aquainted with new FTC rules. 




